Technical Architecture
t54’s agent-native risk engine for x402/AP2 and tLedger. This page introduces the Trustline flow architecture and system components. For implementation details and continuous updates, visit the relevant GitHub repositories.
- Proxy Endpoint:
/risk/*served by the x402-secure gateway (local or production) - Scope: Runtime flow, validation sequence, and decision logic
- Upstream Rails: x402 verify/settle, tLedger settlement
1. System Overview
Trustline implements a multi-tier, committee-based validation architecture designed to assess the trustworthiness of agent-initiated transactions.
It combines sequenced routing, specialized validators, and consensus-based adjudication to provide real-time, explainable, and challengeable risk decisions.
Core Characteristics
- Tiered validation loop (Easy → Medium → Hard)
- Parallel specialization per tier for domain-specific risk analysis
- Consensus-based final decision with confidence scoring
- Optional human-in-loop challenge and re-evaluation flow
2. Core Components
2.1 Sequencer
The Sequencer classifies incoming risk requests by complexity and context, dispatching them to the appropriate validation tier.
Responsibilities
- Classification: Determines initial difficulty tier
- Dispatching: Routes request to validator committees
- Escalation: Triggers higher-tier analysis when confidence is low
- Aggregation: Collects validator outputs for consensus
2.2 Validator Network
Validators are grouped into parallel committees, each specialized in a unique risk dimension.
Validator Specializations
- Injection Detection
- Identity Verification (KYA, device posture, or attestation)
- Consent & Mandate Verification (AP2/x402 evidence)
- Code & Step Validation (tool calls, signature integrity)
- Anomaly Detection (behavioral or contextual deviations)
Each committee executes its validation logic independently, returning structured confidence outputs to the Consensus Coordinator.
2.3 Consensus Coordinator
The Coordinator acts as the judge of each tier. It merges validator outputs to form a unified decision.
Functions
- Aggregates risk scores from multiple validators
- Computes overall confidence and risk level
- Determines whether to approve, decline, or escalate
- Produces the Final Decision Artifact, including optional future liability mapping
2.4 Session & Trace Services
Sessions and traces form the data backbone of Trustline.
-
Session Manager: Creates and manages risk sessions (default expiry 24h, adjustable). Each session anchors the complete life cycle of a transaction evaluation.
-
Trace Manager: Stores reasoning traces, model context, and validation inputs. Multiple traces can attach to one session—allowing challenge and re-evaluation.
3. System Flow
The following diagram represents the complete Trustline risk evaluation process, including session creation, trace submission, multi-tier consensus validation, and challenge handling.
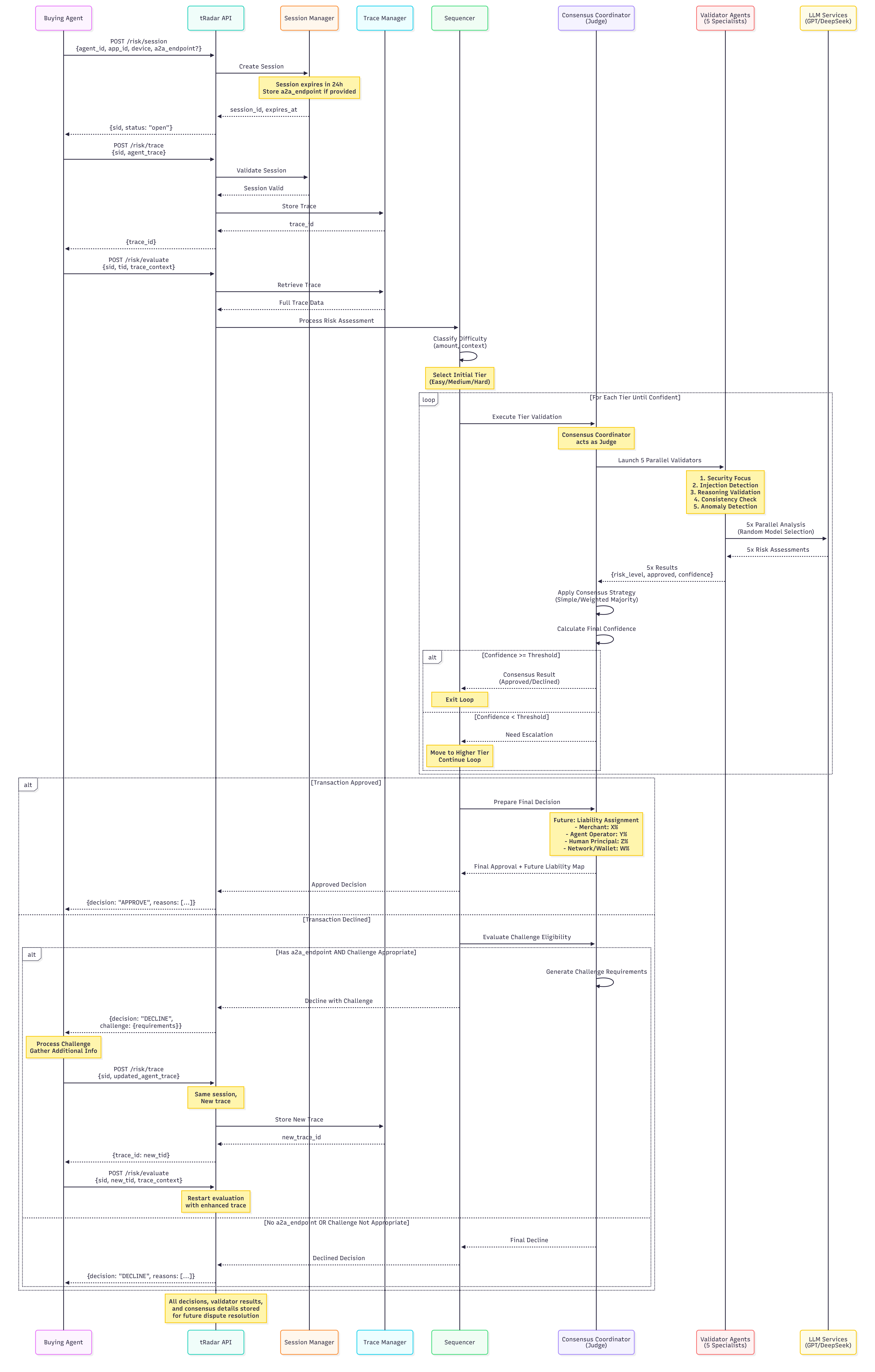
High-Level Summary
-
Session Creation: The system opens a new session with expiration metadata.
-
Trace Submission: Agent reasoning and task context are uploaded and verified.
-
Tier Classification & Dispatch: Sequencer selects the starting tier based on request complexity.
-
Parallel Validation: Specialist validators analyze the trace simultaneously across five focus areas.
-
Consensus Aggregation: Coordinator computes risk level, confidence, and decision outcome.
-
Decision Output: The system issues either an approval or decline, with confidence and validity window.
-
Challenge Loop (If Applicable): When declined, a challenge path can be initiated using new evidence within the same session. The new trace triggers re-evaluation until final decision is reached.
4. Decision Framework
Every evaluation results in a standardized Decision Object containing:
- Decision: Approve / Decline
- Risk Level: Low / Medium / High
- Confidence: Calculated probability score
- Time-To-Live (TTL): Validity window for decision reuse
- Rationales: Summary of validator reasoning
- Challenge Eligibility: Optional field if further evidence is allowed
- Liability Map (Future Use): Outlines role-based accountability (agent, operator, merchant, or network)
5. Integration Notes
-
x402 Integration: Trustline runs in tandem with the x402 verify/settle process and contributes
X-RISK-SESSIONheaders to the payment context. -
AP2 Alignment: Agent consent, mandate, and evidence fields conform to AP2’s evolving intent-verification standard.
-
KYA / Identity Layer: Optional device-based identity (Claire, ASID) can supplement risk signals for challenge and liability reassignment.
6. Related References
Updated 4 days ago